Bitlayer 101 (2): What Makes YBTC Standout?
In the first chapter of our “Bitlayer 101” series, we introduced you to YBTC: a new, yield-bearing representative BTC that brings your Bitcoin’s utility to multiple chains. We briefly touched upon its foundation—the BitVM Bridge—as the source of its security. Now, let’s dive deeper and explore what truly makes YBTC’s security model a generational leap forward.
Not all Bitcoin bridges are created equal. To understand what makes YBTC a breakthrough, we first need a simple framework for evaluating how any BTC bridge works and where its vulnerabilities might lie.
How to Judge a Bridge: The Three Key Questions 🔑
Most bridges use a “lock-and-mint” model. You lock your real BTC in a vault on the Bitcoin network and, by providing proof of this deposit, you mint an equivalent representative token (let’s call it XBTC) on another chain like Ethereum. To get your BTC back, you do the reverse: burn XBTC and present proof to unlock your BTC from the vault.
The security of this entire process hinges on the answers to three critical questions:
- Who controls the locked Bitcoin in the vault?
- Who verifies your deposit to approve the minting of new tokens?
- Who verifies that you’ve burned tokens to approve the release of Bitcoin?
The answers reveal exactly where you’re placing your trust.
Before YBTC: The Generations of Trust
Generation 1: The Centralized Custodian (e.g., WBTC) 🏦
The first bridges rely entirely on a single, centralized Service Provider (SP) to manage the vault and approve all operations.
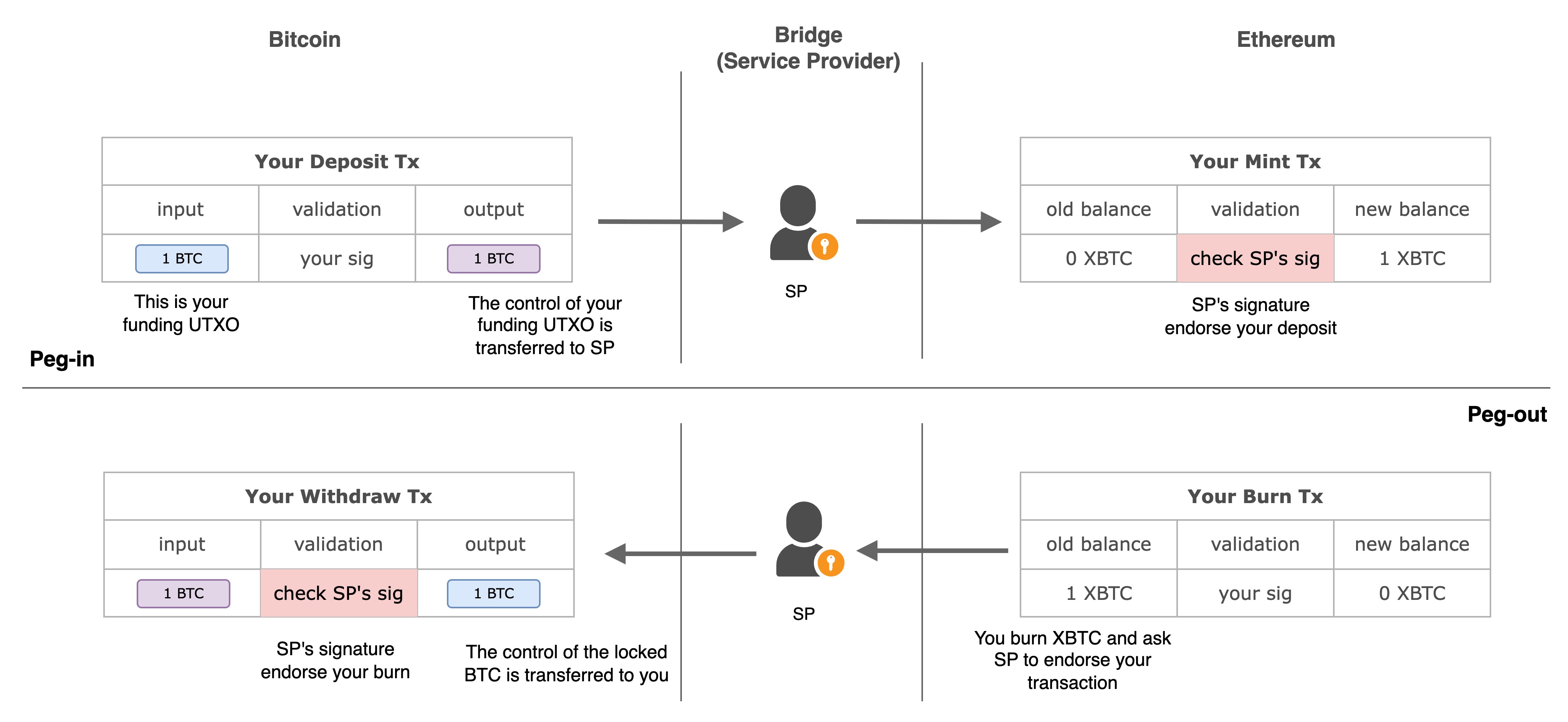
This model requires complete trust in the SP. You must assume they will:
- Honestly approve your mints and withdrawals.
- Never move or misuse the locked BTC.
This introduces two major risks:
- Security Risk: If the SP’s private keys are ever compromised, an attacker can steal all the locked funds, instantly breaking the 1:1 peg.
- Liveness Risk: If the SP goes offline for any reason, all deposit and withdrawal activities halt completely.
Generation 2: The Committee (e.g., tBTC) 🤝
The second generation, including tokens like tBTC, improves on this by replacing the single entity with a small, rotating committee of operators. This decentralizes control and reduces the risk of a single point of failure.
However, at its core, this model still relies on a multisig wallet controlled by a group you must trust. Collusion or a large-scale compromise of the committee members remains a risk.
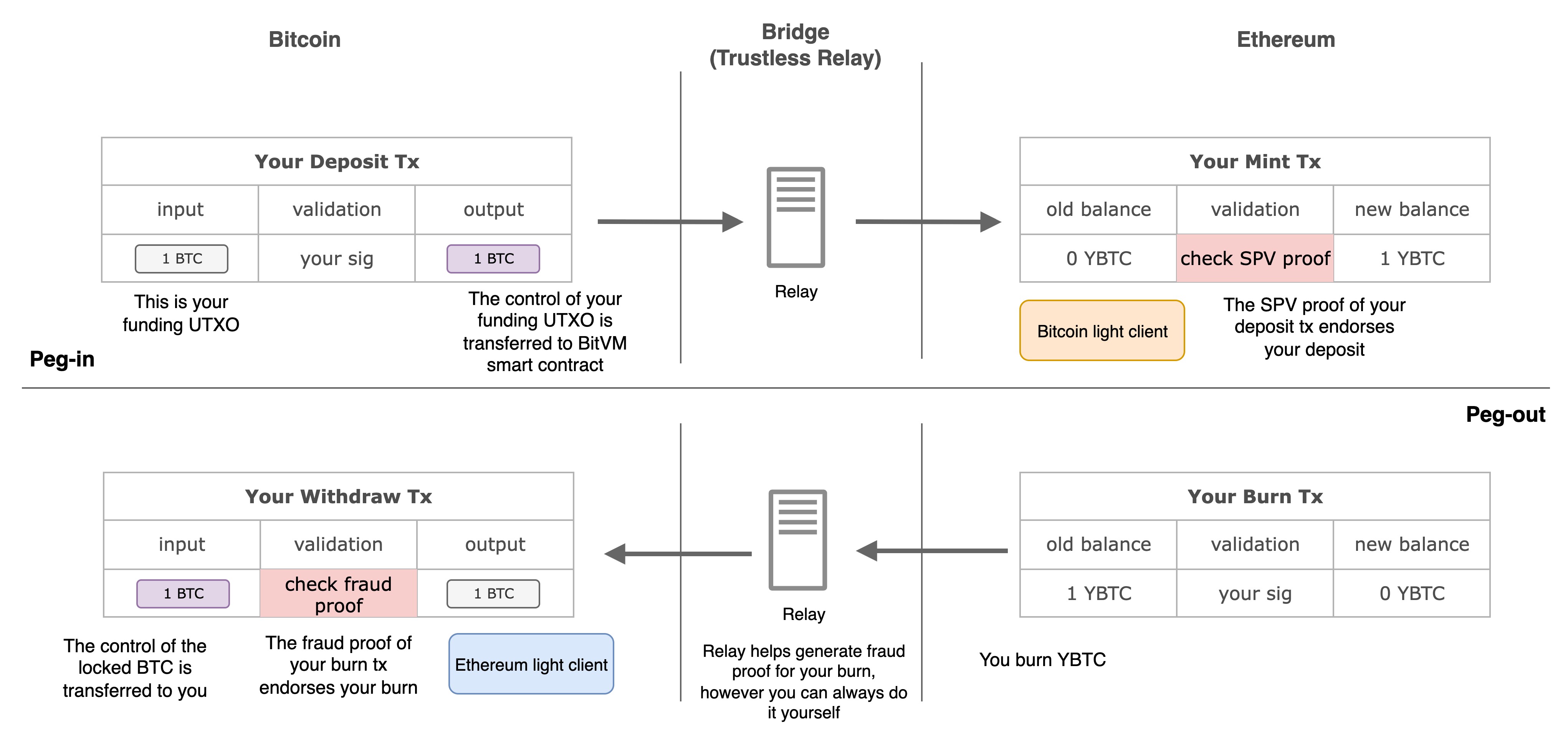
The YBTC Leap: Trusting Code, Not People 🤖
YBTC introduces the third generation of representative BTC by replacing human intermediaries with an autonomous BitVM smart contract.
This smart contract acts as an automated, transparent vault keeper that operates strictly by its code. You don’t need to trust an off-chain company or committee anymore; you only need to trust the verifiable logic of the contract itself.
In this model:
- Users can deposit and withdraw independently and permissionlessly.
- A trustless relay simply passes information between chains, but users can always act as their own relay if needed.
- Deposits are verified using SPV proofs, a secure cryptographic method that proves a Bitcoin transaction occurred.
- Withdrawals are secured by fraud proofs powered by BitVM. This revolutionary mechanism allows anyone to challenge and prove an incorrect withdrawal on the Bitcoin network itself, ensuring the system’s integrity.
We’ll dive deeper into the magic of BitVM and fraud proofs in our next posts!
Summary: The Evolution of BTC Bridging
This table clearly shows the fundamental shift in trust that YBTC represents.
| Generation | Who Controls the Locked BTC? | Who Verifies Deposits (for Minting)? | Who Verifies Burns (for Withdrawing)? |
|---|---|---|---|
| Gen 1: WBTC | A centralized custodian (BitGo) | The custodian’s signature | The custodian’s signature |
| Gen 2: tBTC | A small, rotating committee (multisig) | SPV proof of the BTC transaction | The committee’s multisig signature |
| Gen 3: YBTC | An autonomous BitVM smart contract | SPV proof of the BTC transaction | On-chain fraud proofs powered by BitVM |

